First and foremost, what even is a router-on-a-stick? A router-on-a-stick is a router with only one port. On network diagrams, it is shown with only one line pointing to it, so it looks like a food item served "on a stick":
But if we have fewer ports than a "normal" router, don't we have to compensate for it somewhere else? Yes we do. We must have a managed (or "smart") switch. An unmanaged (or "dumb") switch cannot help a single-port router overcome its single-portedness.
To build an operational network with a router-on-a-stick, we will have to define a few virtual local area networks (VLANs). We will create matching definitions for those networks on the switch and on the router, so the two devices can work together.
The hardware
You can build a router-on-a-stick out of any device with a single network port capable of running OpenWrt with VLANs. You will also need a managed switch.
In this project, we will be using a 10ZIG 4600q thin client as a router. Why this device? No particular reason, other than it running on a quad-core processor (Celeron N3160) with 2 GB RAM and 8 GB eMMC. These are decent enough specifications for a Gigabit OpenWrt router. The device is running OpenWrt 24.10.1.
For the switch, we will use a five-port Netgear GS305E. This is a product that's been around for a while (first released in 2019), but Netgear still sells it; as of this writing (June 2025), it's available new on Netgear's Web site at USD 18.95. It's also widely available in the secondary market. This model is a part of Netgear's "Plus" range, which includes affordable models with limited configurability. So chances are, if we can use this switch with its limited configuration options, we can use any other managed switch.
Here's a group photo of our little heroes:
Plan of work
Before we start configuring things, we need to make a few decisions. Most of these decisions are arbitrary, so you can make up your own parameters.
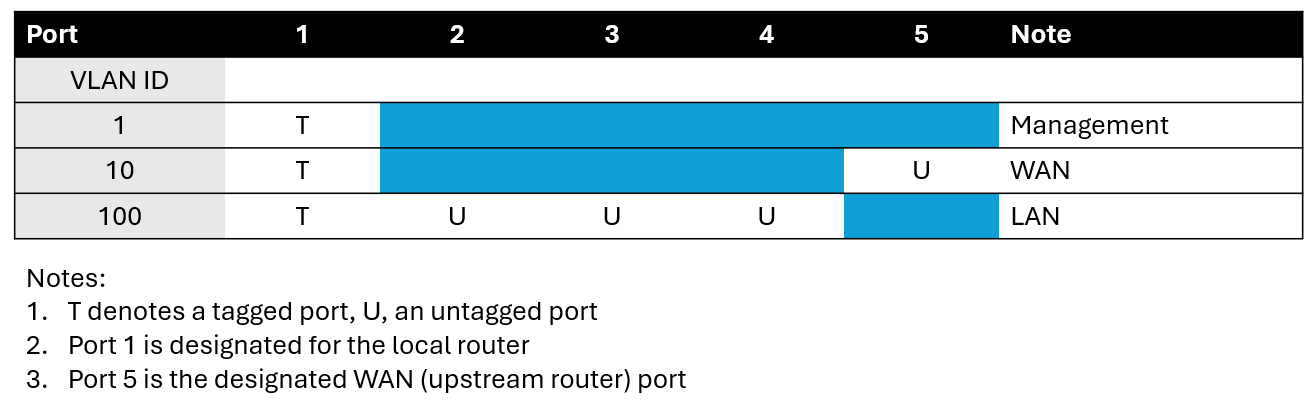
First, how do we want to assign ports on the switch? (To remind, there are five of them.) For this project, we will do:
- Router port (to be connected to the local router-on-a-stick)
- LAN port
- LAN port
- LAN port
- WAN port (to be connected to the upstream device)
Speaking of WAN, we need to remember how the upstream device requires it to be set up. In this case, we have an upstream DHCP server that expects to hear from a DHCP client and assign a dynamic IP address to the client. In other cases, we could have an upstream device that expects a client with a static IP address set manually.
Next, we need three VLAN numbers for the management network (the one we'll be using only for the router and the switch), LAN, and WAN. Let's say we want:
- Management: VLAN 1
- WAN: VLAN 10
- LAN: VLAN 100
VLAN 1 often has some special meaning for a managed switch, but there is no generally accepted rule of what that meaning is. So consult the documentation for your switch to make sure its expectations for VLAN 1 are in line with your plans.
Further still, we need to decide what IP address ranges we want to use for the LAN and the management network. In this project, we will go with 192.168.102.* and 192.168.103.*, respectively. So our router will have two local IP addresses, 192.168.102.1 on the LAN and 192.168.103.1 on the management network. Speaking of the management network, we'll need a short name for it, so let's call it mgmt.
Finally, we need to write down the MAC address for the switch (it's printed on a sticker on the bottom of the switch; let's pretend that it's 12:34:56:78:90:AB) and choose an IP address we'll assign to the switch (say, 192.168.103.2). Note that the IP address must be in the mgmt range, not in the lan range.
Switch configuration
We begin by resetting our switch to the factory configuration, plugging it into our existing local network, and accessing it as instructed on the sticker on the bottom of the switch: go to http://192.168.0.239 in browser and use password as password. The first thing the switch would make us do is change the password, which is a good security practice.
Managed switches are a very diverse bunch, so this part will be deliberately sketchy.
GS305E allows you to define VLANs in two ways, port-based and 802.1Q. We will go with the latter. In a 802.1Q network, a port can be a member of one or more VLANs; in each VLAN where it is a member, it must be either "tagged" or "untagged". (An extended discussion of tagging is probably in order here, but we need to keep going...)
By default, our switch already has VLAN 1 defined and all ports are members of it. So we need to define VLAN 10 and VLAN 100 and assign ports to them, removing their membership in VLAN 1 where necessary. This would take a bit of back and forth, which will take entirely too long to describe and will not be very useful to you if you have a different switch. So let's concentrate on the end result. In the end, we should have a setup like this:
Finally, the static IP address. By default, our switch is a DHCP client. In most cases, this is not a problem, but in our case, it will be. Our switch will be connected to three DHCP servers, two on the local router and one on the upstream device. To make things worse, there's no way to tell the switch where to go for an IP address; everything will be down to which DHCP server the switch will hear from first. Incidentally, if the switch hears first from the upstream device, it will get an IP address on the WAN side, which may make it accessible from the Internet, and that's not good for security.
With all that in mind, we will have to disable the DHCP client (there's a dropdown menu for that on the home page of the management interface) and manually set the following:
- IP address:
192.168.103.2 - Subnet mask:
255.255.255.0 - Gateway address:
192.168.103.1
At this point, we will probably lose connection to the switch (it will no longer respond at its default IP address), so we can turn it off for the time being and go configure the router.
Router configuration
We will configure the router in the most time-efficient way, by directly editing configuration files. By default, OpenWrt has only one text editor, vi, which requires some getting used to. So if you don't feel comfortable with vi, this is the time to work out an alternative. You can install a different text editor (say, nano), or put WinSCP on your Windows computer and use it to edit files on the router remotely, or use some other trick you have up your sleeve (for example, this writer is partial to mc, which combines a file manager, a text editor, and a few other things).
Note that as we make configuration changes, they are not applied instantaneously. Rather, we will make all needed changes first, then reboot the router to load the brand-new configuration in its entirety.
If you're not starting from a clean slate, it makes sense to back up your existing configuration using the backup facility at System >> Backup / Flash Firmware in LuCI, OpenWrt's Web-based management interface.
1. Network configuration
We will begin with the network configuration file, /etc/config/network. First two sections, config interface 'loopback' and config globals 'globals', need no changes, so let's leave them be. The rest of the file, on a single-port machine, is likely to look like this:
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'This is where we start making extensive changes. We already have a bridge in place, so we can set up packet filtering on that bridge (this technique is interchangeably called "bridge filtering" or "filtering bridge").
We need to define three VLANs and assign them to lan (VLAN 100), wan (VLAN 10), and mgmt (VLAN 1) interfaces, remembering to assign appropriate IP addresses to lan and mgmt. Remember, we're assuming that the WAN port will work as a DHCP client; if it is to have a static IP address instead, the wan interface definition would have to be modified accordingly.
Here's what we end up with (to remind, there are config interface 'loopback' and config globals 'globals' sections, which we did not change, in front of this):
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config bridge-vlan
option device 'br-lan'
option vlan '100'
list ports 'eth0:t'
config interface 'lan'
option device 'br-lan.100'
option proto 'static'
option ipaddr '192.168.102.1'
option netmask '255.255.255.0'
option ip6assign '60'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'eth0:t'
config interface 'mgmt'
option device 'br-lan.1'
option proto 'static'
option ipaddr '192.168.103.1'
option netmask '255.255.255.0'
option ip6assign '60'
config bridge-vlan
option device 'br-lan'
option vlan '10'
list ports 'eth0:t'
config interface 'wan'
option proto 'dhcp'
option device 'br-lan.10'In human language, we defined VLANs 1, 10, and 100, and assigned them to interfaces mgmt, wan, and lan, respectively. We also set up IP addresses for mgmt and lan. The wan interface, additionally, has been configured to receive an IP address dynamically from the upstream device.
2. DHCP configuration
In /etc/config/dhcp, we have a section that looks like this:
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'We need to clone it for the other local interface, mgmt. So instead of one section, we will have two:
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'mgmt'
option interface 'mgmt'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'Note that we had to change lan to mgmt in two places (config dhcp 'mgmt' and option interface 'mgmt').
One more thing to do here is to set up a static IP address reservation for the switch. To do that, add the following to the end of the file:
config host
option name 'GS305E'
list mac '12:34:56:78:90:AB'
option ip '192.168.103.2'Obviously, the name can be different, and the MAC address must match that of the switch.
3. Firewall configuration
In /etc/config/firewall, find the config zone statement for the lan zone. It will look like this:
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPTAdd one line (list network 'mgmt') to it, so that it reads:
config zone
option name lan
list network 'lan'
list network 'mgmt'
option input ACCEPT
option output ACCEPT
option forward ACCEPTThis means, we want the same rules that apply to traffic going to, or coming from, the lan interface to also apply to traffic going to, or coming from, the mgmt interface.
At this point, we should turn off the router and prepare to start our new network for the first time.
Cabling
Now we need to make sure our devices are properly connected. With the local router and the switch still off, connect three cables:
- Switch (port 1) to the local router
- Switch (port 2, 3, or 4) to a client machine
- Switch (port 5) to the upstream device
Then, turn on the local router and the switch. With the hardware we have in place, it should take less than 30 seconds for the network to come up.
Testing
If everything went well, you should be able to do the following from a client machine:
- Access the Internet
- Access the local router at
192.168.102.1 - Access the local router at
192.168.103.1 - Access the switch at
192.168.103.2
The local router should be accessible both over HTTP(s) and SSH. The switch we used doesn't have an SSH interface, so it's accessible only over HTTP. Other switches, however, may be HTTPs- and/or SSH-accessible.
